Data transfer is a typical operation in daily digital life, and SFTP is an essential tool for transferring sensitive information.
SFTP stands for Secure File Transfer Protocol. It provides a secure shell (SSH) communication for safe file transfers between a client and a remote server over a public network.
It also enables the efficient management of huge and sensitive files over a given network. SFTP allows users to store, upload, and access files while ensuring their data security and integrity remain intact.
However, its primary use case is to combat threats to data transmitted over the internet.
What Is SFTP?
SFTP is an SSH file transfer protocol technology used to provide a high level of security when transferring files. To achieve this objective, SFTP operates in a client-server architecture, guaranteeing that the client and the host machine are both validated and authenticated.
The Internet Engineering Task Force designed SFTP as an extension of SSH. As a result, understanding SSH is essential for grasping SFTP’s working mechanism.
The SFTP file transfer process involves four main components and procedures that establish a secure connection between two endpoints:
- SFTP client software. SFTP clients initiate requests to the server. They are equipped with software that contains SSH programs to facilitate authenticated SSH connections to SSH servers.
- Server host. When you use an SFTP server, it typically incorporates an SSH implementation. The host server waits passively, listening on a designated SSH port (port 22) for an SFTP client request. In the event of a request, the client and server identities are verified.
The client-server verification process occurs via a three-way transmission control protocol (TCP) handshake. The TCP handshake in the transport layer makes it possible to establish and forge connections across the internet and network layers. - Establishing connection. The connection between the client and server is only established when both parties have been authenticated. Subsequently, the connection between the client and server is encrypted. File transfer occurs only after this encryption is complete.
- Firewall configuration. When using an SFTP connection, your firewall must be configured to communicate successfully between the SFTP server and clients. For instance, the firewall has to be configured to accept incoming traffic from the default SSH port 22.
These are the general components that must be in place for an SFTP transfer to succeed. However, there are other core technology practices that are integrated into the SFTP transfer process as well.
The key highlights of the SFTP cybersecurity process include:
Authentication—Once an SFTP client connects to a server, it must provide validation credentials that confirm its identity.
However, this isn’t a one-way process.
The SFTP process also authenticates the user (client) and the server (host machine). To provide the secure authentication necessary to prevent unauthorized access, it uses passwords, SSH keys, or a combination of both.
Encryption—SFTP facilitates secure file transfers between local and remote systems through SSH encryption.
Data integrity and confidentiality—In addition to encryption, SFTP uses hashed cryptographic checksums and message authentication codes (MACs) to verify the integrity of the transmitted data payload packets.
Robust file management—The SFTP client can perform a host of administrative tasks on files in the SFTP server, like copying, editing, and deleting. In addition to securely transferring files, these file management capabilities have made it attractive to developers and system administrators.
Improvements over FTP—SFTP is a significant improvement over its predecessor, the legacy File Transfer Protocol (FTP). While FTP was once the gold standard for network file transfer, it has many innate weaknesses that make it an insecure protocol today.
For instance, it transmits plain traffic by using port forwarding to create an encrypted connection between the client and the server—and the data tunneling process used to achieve this process creates security risks.
Moreover, FTP is also a less reliable method to implement security because it doesn’t deal with the problem of user or host identification verification. Among other things, FTP is susceptible to port stealing, packet sniffing, and brute-force attacks.
Alternatively, SFTP uses packed-based transmission rather than an outdated text-based transmission.
SFTP’s underlying technologies
SFTP’s central underlying technology is the aforementioned secure socket shell, or SSH. SSH is a cryptographic network protocol used to facilitate access to digital resources and files over an unsecured network.
In addition to encrypting the transmitted data, SSH also encrypts passwords and identities. This is useful for command-line executions, remote logins, and other network service purposes. When you mention SSH in the context of SFTP, you are referring to the network protocol and the SSH handshake process that makes secure file transmission possible.
SFTP and SSH overlap so much that they appear to be two peas in a pod. This is because SSH is SFTP’s binding agent during the file transmission process. While they are intertwined in the sense that they both have a similar objective in securing communications during message transmission, they also harbor vital differences.
For instance, SSH operates in the transport layer, while SFTP lives in the higher-level application layer of the Transmission Control Protocol/Internet Protocol (TCIP/IP) model.
SSH provides secure file transfers by encrypting the data stream. It exclusively uses asymmetric key cryptography, while SFTP can operate with symmetric algorithms such as Triple DES and the Advanced Encryption Standard (AES) algorithm. AES is a robust standard that’s been widely adopted by the United States government to protect classified information.
SSH adopts a pair of keys, one private key for encryption and one public key for decryption. This way, key storage becomes less of an issue than symmetric key encryption.
Applications that use SSH are typically based on client-server architecture, which fits right within the domain of SFTP. Although HTTPS (Hypertext Transfer Protocol Secure) is an alternative network protocol with more widespread adoption, SSH is a more secure alternative than providing credentials over HTTPS.
How SFTP safeguards the file transfer operations
SFTP doesn’t provide a high level of protection during file transfer by accident. In addition to encryption, it embodies core design and implementation imperatives that elevate its security.
SFTP ensures the file transfer proceeds only when the client and server connections have been authenticated.
Here are the various ways SFTP secures the file transfer process:
Using only one secure connection—SFTP uses a secure shell data stream to establish a secure connection with a single open port. This single connection ensures the presence of data security and integrity throughout the file transfer process. Hence, SFTP is able to fortify security through this single connection and reduce its attack surface.
Checks against tampering—Hacking involves nefarious activity that goes beyond just stealing information. In addition to encryption, SFTP prevents message tampering by applying message authentication code to its hashed payloads.
Multiple authentication methods—While FTP doesn’t address the problem of user/host identification, SFTP solves it while allowing you to choose either SFTP passwords or SSH keys for secure authentication. The SSH public and private key pair are used to initiate a secure handshake between the local SFTP client and the remote server.
By using these authentication procedures, SFTP provides much stricter security.
Username and password authentication—Here, the authentication for the file transfer service is done through the credentials of the user. This necessitates the creation of user service accounts on the SFTP server.
It is a basic system that’s simple to set up and implement. To strengthen it, organizations typically mandate rigorous password policies that demand specific criteria be met—such as rules on character length, the inclusion of special alphanumeric characters, how frequently passwords may be changed, and so on. Multi-factor authentication (MFA) may also be used to strengthen this process.
SSH authentication—This is authentication by the SFTP client. Since SSH and SFTP are intertwined, this is generally the better option for SFTP authentication. For instance, the key pair generated by SSH is typically 4096 bits in length, which is much longer than the length of a common password.
Whether you choose passwords or SSH keys, the overarching objective here is to prevent unauthorized access. In this authentication mode, the private key resides with the SFTP client, while the public key is kept on the server.
Authentication by SFTP server—A host-based authentication which uses the private host key, this process underscores that client verification is not the only requirement for making file transfer secure. Host identity verification compels the server to “prove” its identity to the client and validate that the remote system it connects to is a known entity.
The host key is persistent, so a new key isn’t generated when a new session is initiated. Host identification verification is necessary because it mitigates man-in-the-middle (MIMT) attacks that alter the relayed information mid-transmission.
SFTP use cases and why it is a crucial technology
Technical wizardry can look mesmerizing, but it only becomes helpful when it demonstrates its usefulness in real-life scenarios. SFTP has gained popularity because it has found compelling use in the business arena.
Here are some of the most common use cases for SFTP:
Safeguarding sensitive data—Modern businesses need to collaborate with other entities for cross-pollination of ideas, supply chain partnerships, and specialized expertise so they can deliver value to customers.
However, sharing proprietary information with vendors, contractors, and third-party suppliers comes with risks of unauthorized access, data leaks, and data breaches. These threats risk exposing vital trade secrets and user data that confer competitive advantages.
Therefore, businesses must safeguard their intellectual property, company secrets, and proprietary information—including the financial and personally identifiable information of their customers. SFTP, with its SSH-encrypted communications and requests for authentication, goes a long way to mitigate these risks.
Increase in overall file security—Much like file transfers, data in transit faces many threats en route to its destination. Hackers have adopted both simple and sophisticated methods to exploit file transit vulnerabilities, starting with eavesdropping, impersonating, intercepting data, and stealing login credentials via readily available sniffing software.
Other methods are more sophisticated, such as server hijacking, data tampering, and man-in-the-middle (MITM) attacks. The latter often involves the injection of malicious proxy software to subvert data integrity through tampering.
Nevertheless, SFTP shields communications so there’s little or no vulnerabilities, thus minimizing the likelihood of a successful attack at any point in the data transfer process.
Meeting Compliance Regulations—The deluge of data breaches in the past decade has raised a lot of awareness and concerns over data protection, as well as customer data sensitivity and the need for privacy. It also compelled regulatory authorities worldwide to enact far-reaching data protection measures.
The more popular ones are called GDPR, HIPAA, PCI DSS, SOX, and CCPA. (Like many things throughout this piece, you may need to chuck those into Google.)
As a result, there are many security standards companies must adhere to or risk facing stiff fines and penalties. One of these is the need to meet regulatory requirements that data transfers occur securely across the internet and internal networks.
While these regulations don’t identify a specific tool in their security guidelines for internet-facilitated file transfers, SFTP can more than meet the standards outlined. It mitigates many of these problems and enables organizations to maintain regulatory compliance with these laws, especially with regard to file transfer compliance.
Automated file transfer operations—Organizations often execute thousands of SHH transfers on a daily basis. For instance, large enterprise organizations could have up to 5 million daily automated SSH logins. Most of these would be tedious to execute manually without the benefit of using SFTP to automate their operations.
Some other tasks that can be automated with SFTP include automatically copying data to disaster recovery systems and implementing nightly backups of many other systems.
Using an SFTP Client
An SFTP client is the software that allows users to make a secure connection with the SFTP server to protect data during transmission.
The client subsequently allows users to transfer files to and from remote machines running SFTP servers.
SFTP clients also enable users to perform file operations over a non-secure network like TCP/IP. Examples of those operations include the following:
- Uploading and downloading files and directories
- Exploring and navigating local and remote file systems
- Managing content management systems like WordPress.
Most SFTP clients are native applications installed on operating systems like Windows. Others, like Chrome’s sFTP, are plugins that can be activated through the browser.
Choosing an SFTP client is only the first step in the process of transferring files securely. You first need to set up the SSH keys that would be used in the process and subsequently add them to the ssh-agent before copying its public key to the target host server.
Since SSH uses asymmetric encryption, the private key resides on the SSH client software, while the SSH server stores the public key.
Step 1: Setting up the SSH keys
Git is an ideal application to practice setting up SSH keys, as it provides a secure shell as an inbuilt functionality. Therefore, users can use SSH keys for authentication rather than traditional passwords to access and write data to remote code repositories.
The first step is generating the SSH key on the local machine.
Launch the terminal
In the following illustration, we used the terminal to generate an SSH key for a GitHub account. Most terminal applications shipped with standard operating systems like Windows and Linux come with SSH suite installed.
Execute commands/steps to start the key generation process with the Ed25519 algorithm
OpenSSH, an open-source library and connectivity tool for the SSH protocol, handles the key generation process. OpenSSH supports various types of keys. In this instance, we used ecdsa, which is a key generated with the Elliptic Curve Discrete Logarithm Problem algorithm.
ssh-keygen -t ed25519 -C “your_email@example.com”
This command creates a new SSH key using the supplied email address as a label.
If the command was successfully executed, your terminal should generate responses similar to those in the image below.
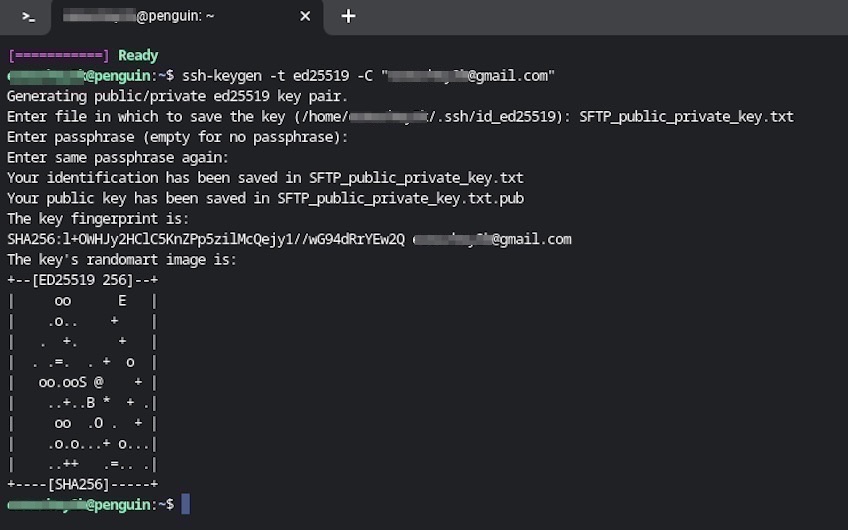
Upon successful execution, you’ll be prompted to enter a file location to save the key and a passphrase to protect it.
Step 2: Adding the new SSH Keys to the ssh-agent
While you’ve provided a passphrase to protect your SSH keys, most people find it mildly annoying to enter it each time. This is where an ssh-agent comes to the rescue. The ssh-agent acts as a key management broker and is responsible for holding the private keys.
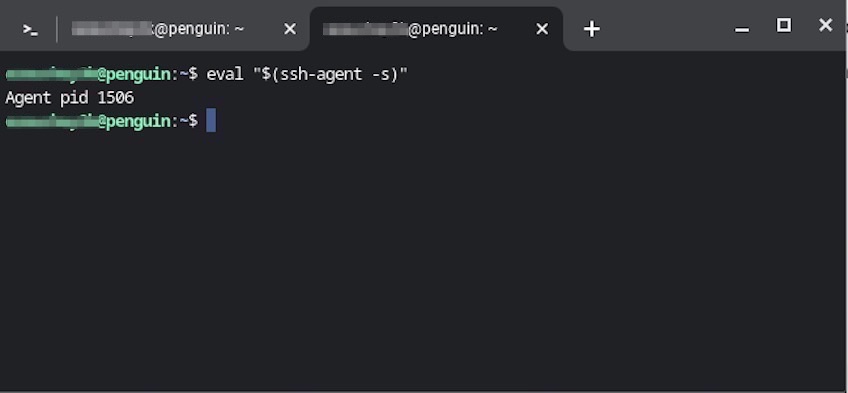
However, you need to ensure the ssh-agent is running in the background before attempting to store the generated keys.
Simply type: eval “$(ssh-agent -s)” at your terminal prompt, as seen in the image below.
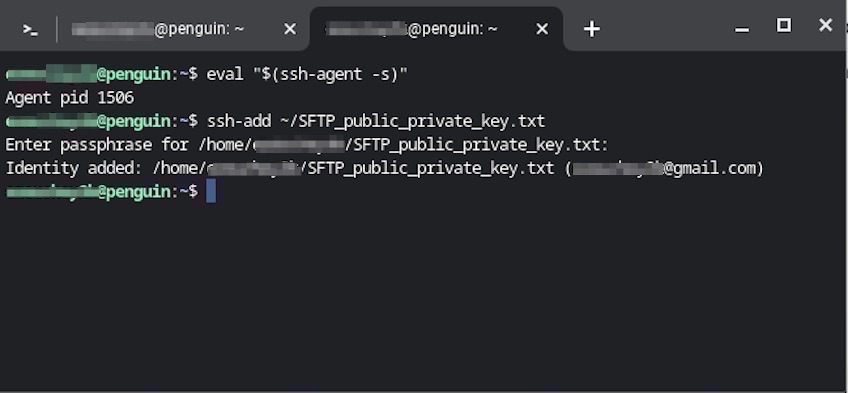
After you’ve verified your ssh-agent is running, use the ssh-add helper program with the existing key, as shown below.
Step 3: Copying the public key to the SSH server
This is highly idiosyncratic and the steps will depend on the server and host platform you are using. Therefore, you’ll have to look up how to accomplish this for your individual setup.
If all goes well, you’ll gain a lot of the advantages that come with using an SFTP client.
Benefits of using an SFTP client
Quick and safe data transfers—Apart from cybersecurity concerns, transferring large volumes of data requires significant time, effort, and resources. SFTP clients help alleviate this problem by streamlining and even automating the process.
Effective server administration—The SFTP client is a tool that effectively and efficiently enables developers and system administrators to transfer system and program files securely and with little hassle. This is vital for sensitive files that contain business requirements, trade secrets, and proprietary information.
Seamless integration—Most SFTP applications, including their clients, are able to integrate with other third-party applications like firewalls and VPNs. This allows content managers, developers, and system administrators to increase efficiency, operational capacity, and overall productivity.
Popular SFTP Clients
SFTP clients provide you with direct access to files on your website and remote servers. These tools provide efficient file management that boosts productivity, especially if you are involved in development, web design, and content management.
The most popular SFTP clients are able to do the following:
- Perform file management tasks such as uploading, downloading, editing, and changing file permissions.
- Perform file integrity checks, including session recovery initiation for dropped sessions.
- Safeguard files during transmission by providing encryption, authentication, and other protocol support.
- Provide accountability and non-repudiation with logging for compliance, auditing, and troubleshooting.
- Offer users the ability to upload multiple files through the root directory of a content management system like WordPress.
Many SFTP clients are also free or available for a competitive price with a free trial period included.
An overview of the most popular SFTP clients
- SolarWinds Solar-Putty—This free file transfer utility is flexible and includes SCP, FTP, and SFTP options.
- WinSCP—WinSCP is an FTP and SFTP client exclusively for Windows. This graphical user interface (GUI) client supports protocols such as SFTP, FTP, WebDAV, SCP, and S3 protocols. It also provides server and advanced functions like scripting, connection tunneling, and task automation.
- Cyberduck—Cyberduck is an SFTP/FTP file client that works on both Microsoft Windows and Apple Mac systems. Cyberduck supports a variety of platforms such as OpenStack Swift, Backblaze B2, Microsoft Azure & OneDrive, Google Drive, WebDAV, Amazon S3, and Dropbox.
- sFTP Client—This Chrome SSH extension allows users to turn their Chrome browsers into an SSH client, offering users basic SSH protocol capabilities as a plugin.
- GoAnywhere SFTP client for managed file transfer (MFT) solutions—For securing, streamlining, and automating file transfers.
Extra functionalities with paid software
Customers generally pay for premium and advanced features that boost their productivity and offer heightened convenience, including enterprise features that help scale business operations.
Regarding SFTP software, here are some features customers typically fork over extra money for:
- Advanced security—This permits or blocks usage based on country or geographical region, deploying custom SSL certificates for custom domains. Deployment of on-premise agents to facilitate granular security behind firewalls and network environments.
- Custom compliance and auditing—Allows the organization to meet the stringent compliance requirements and the flexibility to craft custom data governance policies for its enterprise.
- Advanced file transfer integrations—This includes, for example, using integration platform as a service (iPaaS) systems to foster the usefulness of hundreds of third-party applications.
- Global and international support—This adds multi-lingual support and the ability to store files globally.
The top three SFTP clients
SolarWinds Solar-Putty
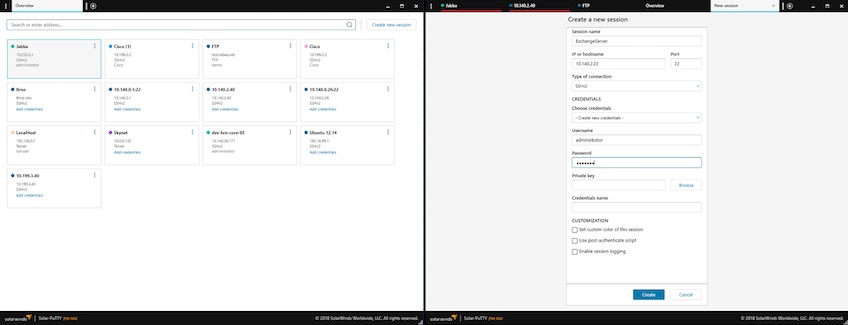
SolarWinds Solar-Putty is a free, standalone terminal emulation built on top of a popular and free SSH client, PuTTy.
Solar-Putty is an extensive improvement over PuTTy that enables you to use SFTP, FTP, Telnet, SSH, and secure copy protocol (SCP) to connect to resources.
SolarWinds Solar-Putty standout features
- Session/credential management—Provides the ability to save credentials like private keys and passwords to any session to facilitate easy, authenticated logins.
- Multiple session management—Supports the ability to manage multiple active connections from a single running instance of its console.
- Post-connection scripting—This enables you to automate the use of scripts when a valid connection is established.
- Windows integration—Allows you to discover your saved sessions thanks to the Windows Search integration. Moreover, features like ipMonitor from SolarWinds offer the ability to track key metrics with round-the-clock Windows application monitoring and integrations.
Pros
- No installation required.
- Allows teams to manage remote sessions in a professional manner.
- Includes a browser-based interface for user-friendliness.
- Has the ability to recall saved PuTTy sessions.
- Keeps all the advantages of the original PuTTy, with added enhancements.
- Has multiple integration capabilities to connect to virtually any server.
Cons
- The interface is geared towards network professionals, not ordinary users.
WinSCP
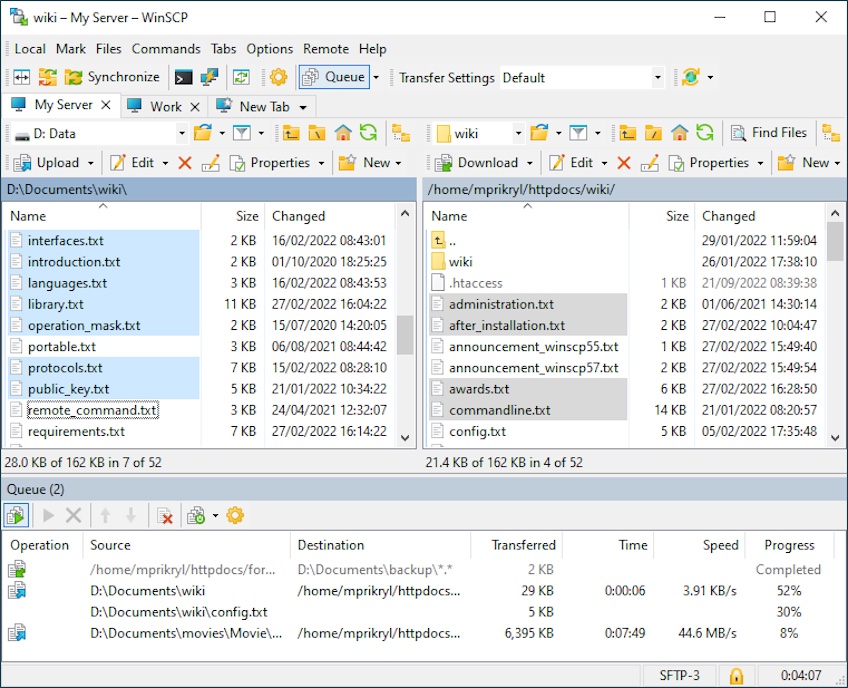
WinSCP is a popular Windows client for file transfers. It offers FTP, SFTP, and SCP protocols—along with a basic file manager functionality that includes your typical copying, pasting, and deleting operations.
While WinSCP is simple, it also offers advanced features such as timestamp conversion, file synchronization, remote editing, and administrative restrictions.
WinSCP standout features
- Robust CLI capabilities—Provides a command line scripting version popular with developers and system administrators.
- Application-based integrations—Offers users the ability to integrate WinSCP into applications based on Windows and PuTTy.
- Task automation—WinSCP is equipped with vigorous scripting capabilities.
- Sophisticated file transfer features—These include directory caching and binary transfer modes. It also allows you to set up individual shell sessions to execute remote commands.
Pros
- Small and light footprint with minimal consumption of system resources.
- Open-source and free.
- Combines CLI and GUI to cater to different user preferences.
- Has a large user base, which translates to robust institutional knowledge and support in online forums.
Cons
- No support for terminal emulation.
- Only available on Windows.
- Lacks sophisticated text editing features.
- It can easily get bogged down when transferring large files.
- The user interface could do with a vast improvement.
Cyberduck
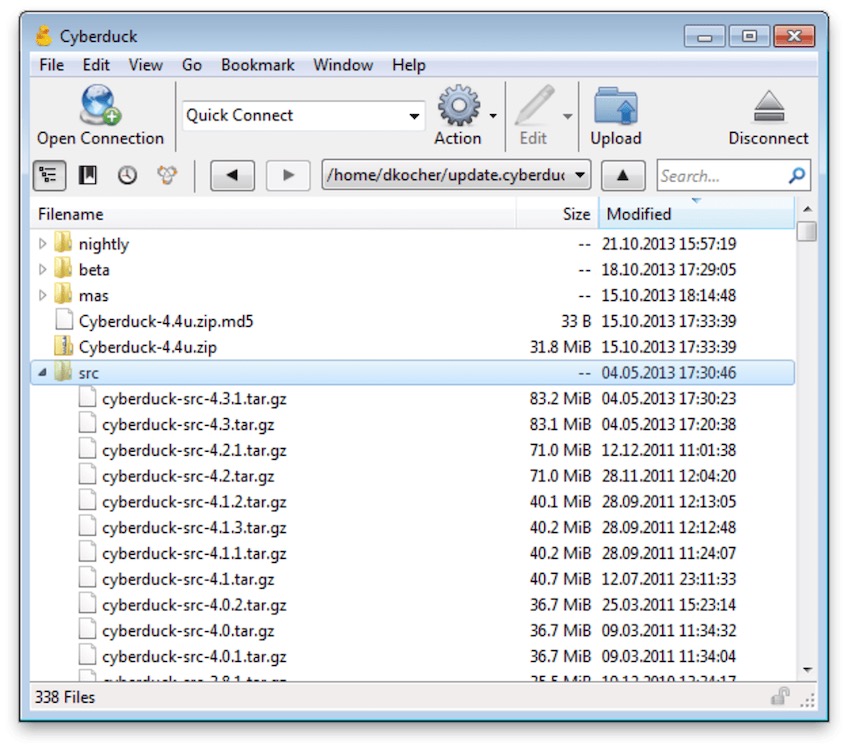
Cyberduck is a free, open-source FTP, FTP-TLS, and SFTP browser. It is renowned for its slick, minimalist user interface that lacks visual clutter. Although Cyberduck was initially designed for the Mac, it has been extended to include the Windows OS. One of its primary strengths is the ability to link to the profiles of most of the leading web hosting services.
Cyberduck standout features
- Easy file management—Besides user-friendly drag-and-drop object features, Cyberduck also provides cut-and-paste functionality.
- Multiple integration points—In addition to Windows integration, Cyberduck offers support for common platforms so you can connect to any server. These include Dropbox, Oracle Storage Cloud Service, Google Drive, OneDrive, Microsoft Azure, OpenStack Swift, Amazon S3, Blackblaze B2, and more.
- Editor preferences—Provides integrated support for external document editors, making it easy for users to edit files seamlessly and change content quickly with their favorite editing software.
- SSH with keyboard-interactive authentication—Supports one-time passwords and keyboard-interactive authentication with prompt parameters for human operators.
- Client-side encryption—This feature allows users to deploy interoperable vaults to fortify data security on any server or cloud storage platform they use, via a cloud encryption platform called Cryptomator 6.
Pros
- Intuitive and user-friendly UI with minimalistic design.
- Compatible with both Mac and Windows operating systems.
- Offers the option of encrypted credential storage, especially on the client side.
Cons
- Limited platforms with no support for Linux-based systems.
- Cyberduck’s sophisticated security features, unfortunately, tend to slow it down.
- Improvements are needed with its drag-and-drop feature.
Of the three, SolarWinds Solar-Putty is probably the best. Not only is it free, but it also boasts a rich set of sophisticated SFTP client features. Although some might find its interface a bit complex, it has a low learning curve—so can be adopted easily by novice and highly technical users alike.
